Hi,
I'm testing in OCSReports 2.8 and I found one insertion point of javascript code, it leads perform XSS Reflected above the home site and others. The issue it's about:
Using the next URL you can inspect the code through dev tools on your browser and check it. URL: http://10.220.33.62/ocsreports/index.php?xss='</script><script>alert(1)</script>
Below, you can see how reflects the payload send by url.
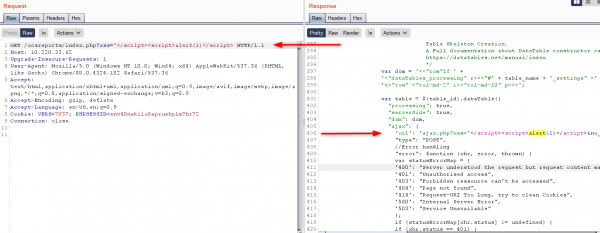
However, the exploration not is easy, the browser should be with XSS filter setting OFF. I ran it in IE, and this is the result. An attacker would be perform bypass the browser controls to gain more impact for this vulnerability and to access any of the user's data. If the victim user has privileged access within the application, then the attacker might be able to gain full control over all of the application's functionality and data.
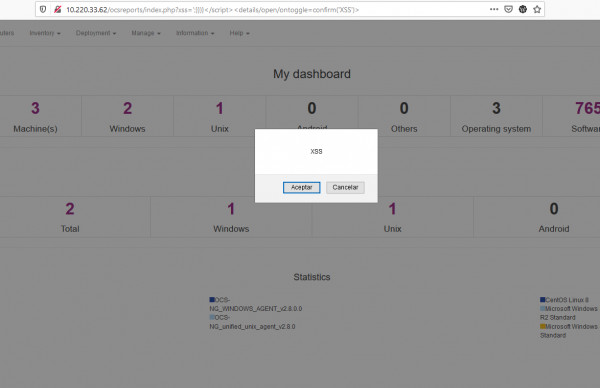
regards.
Server information
Operating system
- OS Name :
- Version :
- RAM installed :
- Free RAM :
- CPU :
- Distribution :
- Linux x86_64
- 4.18.0-193.28.1.el8_2.x86_64
- 3778 MB
- 2972 MB
- Intel(R) Xeon(R) Silver 4114 CPU @ 2.20GHz
- CentOS Linux 8 (Core)
Software
- PHP Version :
- Web Server :
- Database Server :
- Version OCSReports:
- 7.2.34
- Apache/2.4.37 (centos) mod_perl/2.0.11 Perl/v5.26.3
- MariaDB Server version 10.3.17-MariaDB
- 2.8